Posted: January 20, 2022
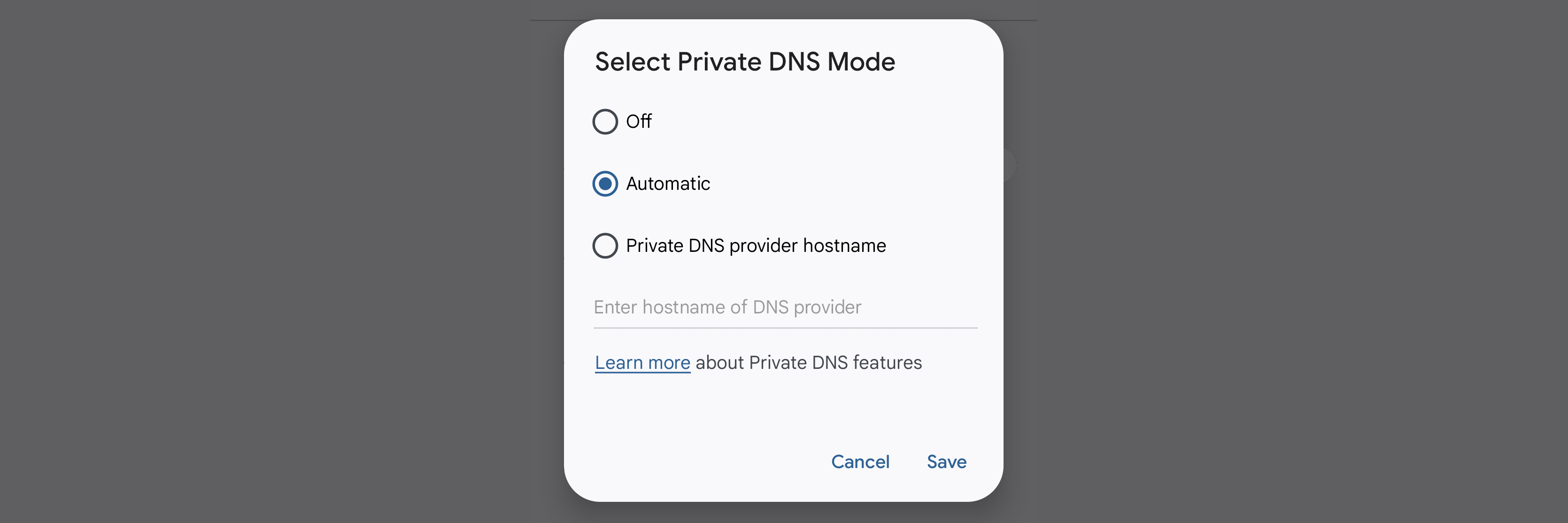
Starting with Android 9 Pie, a new feature called “Private DNS” was introduced.
On Android 12, you can find this setting at: Settings → Network & internet.
This solves the problem of your Internet provider of the moment – whether it be your mobile phone carrier or your WiFi host – snooping on your name lookups (such as cancerInfo.example.com) and exploiting that information.
Private DNS Assures Your Access Privacy
Name lookups resolve names such as www.amazon.com to their location on the Internet. This is sensitive information.
All your Internet access (including all the websites you visit) can be determined from your Internet name lookups. Knowing your lookups won’t reveal what you saw or said, but it will divulge where you went.
If an Internet provider determines you visited ford.com and chevrolet. com then they may exploit that knowledge to start pushing car and truck ads at you.
This information exposure occurs in one of two possible ways.
First, name lookups typically are unencrypted. If your Internet provider is doing packet sniffing then they can look inside your requests and infer where you are visiting. Even if you only visit secure https websites, your name lookups will reveal your activity.
Second, when you connect to the Internet, your Internet provider typically tells you what server to use for name lookups. That’s often their own server. If they log or capture lookup information on that server, then they can get your lookup activity without doing packet sniffing.
Android Private DNS solves these problems in two ways.
First, it uses encrypted DNS over TLS queries, rather than the more common unencrypted queries. This protects you from sniffing.
Second, it directs your DNS queries to a trusted name server, instead of the one that your Internet provider specifies. By default, it uses the Google Public DNS server at dns.google. If you’d prefer not to use that server, you can specify an alternate. 1dot1dot1dot1.cloudflare-dns.com is a popular choice.
Private DNS is a great feature to assure your privacy when you are connected to the Internet through some other provider – such as your phone carrier or a WiFi host.
The Problem with Local Resources
The problem with the Private DNS features is that it interferes with accessing local resources on trusted connections.
My local home network has resources I’d like to access on my Android devices. This includes wiki.chez-rufus.lan (the wiki where I keep personal notes) and jellyfin.chez-rufus.lan (the music and movie media server I’m setting up).
I put all my local resources in the .LAN top-level domain (TLD). The .LAN TLD is reserved and will never appear in the global DNS. So it’s safe to use for private resources.
Those resources can be accessed only if you are connected to my home network. Those DNS names (like wiki.chez-rufus.lan) are resolved by the name server on my home network and are not known in the global DNS.
Yet, if you connect an Android device to my secured home WiFi – which puts you on this network – you can’t access these resources. That’s because Secure DNS overrides the name server selection and gives you a public DNS server that doesn’t (and shouldn’t) know about my local resources.
This is not just a WiFi problem. I set up a VPN back to my home network, so when I’m roaming I can connect to these resources. But with Private DNS, I cannot get name resolution for these resources.
The end result is that even though my Android device can access my home network, it is unable to locate the resources on that network. That’s a problem.
Workaround Wanted
There are a couple of possible workarounds, but I find them all unsatisfactory.
You can go into your network settings and manually disable Private DNS when connecting to a trusted network. That’s an unlikely thing to do every time I connect to my home WiFi or VPN. Even worse, if I did, I’m sure to forget to re-enable the secure setting when I’m done.
The second unsatisfactory solution is to use the Tasker app. This has been done. Unfortunately, it’s hard to set up and it requires some developer-level fiddling with adb that I’m not willing to do. (I don’t want to install the Android Studio developer environment just for this.)
The solution I’d like to see is for Android to provide the ability to override the Private DNS setting on a per-connection basis. That way I could leave the global setting on “automatic”, but turn it off when connecting to a trusted WiFi network or bringing up my VPN.
I hope this feature finds its way into a future Android release.